Definition
Access Certification, also known as Access Review or Entitlement Review, is the process of periodically reviewing and validating user access rights to ensure that individuals have appropriate access to systems, data, and applications. It is a critical part of identity and access management (IAM) aimed at preventing unauthorized access and ensuring compliance with security policies.
Detailed Explanation
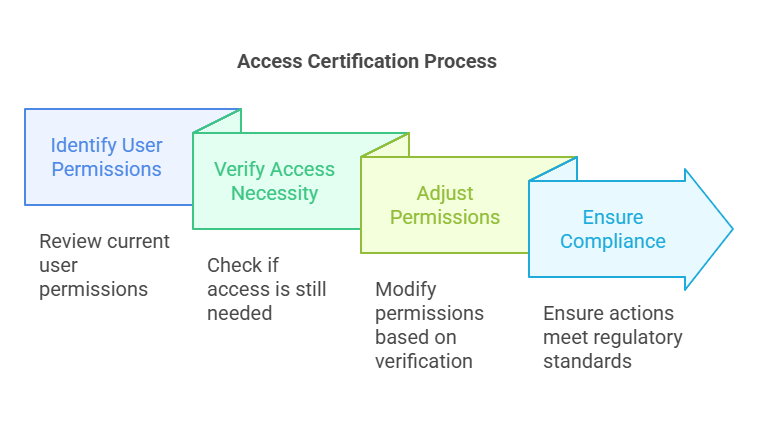
Access Certification involves verifying that a user’s access level matches their job responsibilities and organizational role. This process ensures that employees, contractors, and other users do not retain access to sensitive systems or data when it is no longer required. Organizations conduct access reviews to minimize the risk of privilege creep, where users accumulate unnecessary permissions over time.
The certification process typically involves managers or system owners reviewing a list of user permissions and confirming whether the access granted is still necessary. For instance, when an employee changes departments or leaves the company, their access rights should be reviewed and adjusted to reflect their new responsibilities or removed entirely.
Access certification is particularly important for meeting regulatory compliance requirements, such as GDPR, HIPAA, SOX, and other data protection regulations. It helps organizations maintain a secure environment by preventing data breaches, insider threats, and compliance violations.
Key Characteristics or Features
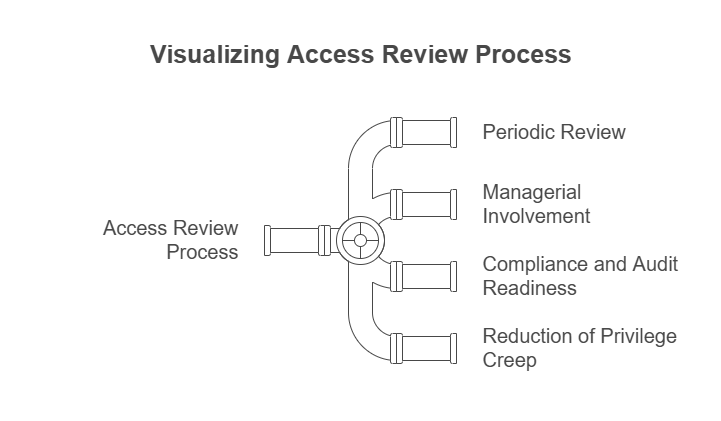
- Periodic Review: Conducted on a regular basis (e.g., quarterly, annually) to ensure that access rights remain appropriate.
- Managerial Involvement: Managers or designated reviewers approve or revoke access based on the user’s role and responsibilities.
- Compliance and Audit Readiness: Provides a documented trail of access reviews, demonstrating adherence to security policies and regulatory requirements.
- Reduction of Privilege Creep: Helps prevent users from accumulating excessive or outdated permissions, thereby reducing the attack surface.
Use Cases / Real-World Examples
- Example 1: Financial Institution Compliance
A bank conducts quarterly access reviews to ensure that tellers do not have access to customer financial records beyond what is required for their role, in line with SOX compliance. - Example 2: Healthcare Data Protection
A hospital uses access certification to review who has access to electronic medical records (EMRs), ensuring compliance with HIPAA and minimizing risks associated with unauthorized access to patient information. - Example 3: Cloud Services Access Management
An organization using cloud services conducts access reviews to ensure that terminated employees or transferred personnel no longer have access to sensitive cloud-based applications or data.
Importance in Cybersecurity
Access Certification is crucial for maintaining a secure IT environment by ensuring that users only have access to the resources necessary for their role. It helps organizations to:
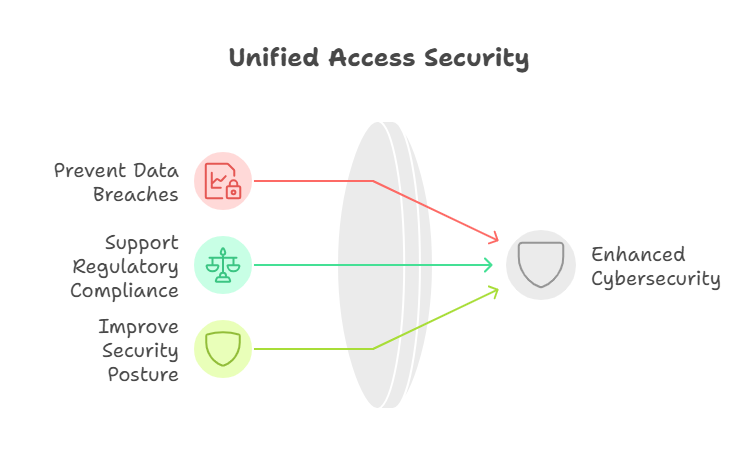
- Prevent Data Breaches: By removing unnecessary access rights, organizations minimize the potential for unauthorized data access and insider threats.
- Support Regulatory Compliance: Regular access reviews are often mandated by regulations, helping organizations avoid fines and legal penalties.
- Improve Security Posture: Access certification is part of a broader identity and access management strategy, enhancing overall cybersecurity by managing access rights proactively.
Related Concepts
- Identity and Access Management (IAM): Access certification is a key component of IAM, ensuring that access permissions align with user identities.
- Role-Based Access Control (RBAC): Access certification often leverages RBAC principles to validate that users have the correct access based on their roles.
- Privilege Management: Works alongside access certification to manage and monitor elevated privileges for sensitive systems.
Tools/Techniques
- SailPoint IdentityNow: A popular IAM solution that automates access certification, making it easier for organizations to conduct reviews.
- Oracle Identity Governance: Provides robust access certification features to ensure compliance and manage user entitlements.
- Okta Lifecycle Management: Facilitates automated access reviews and certification processes, integrating with various cloud services.
Statistics / Data
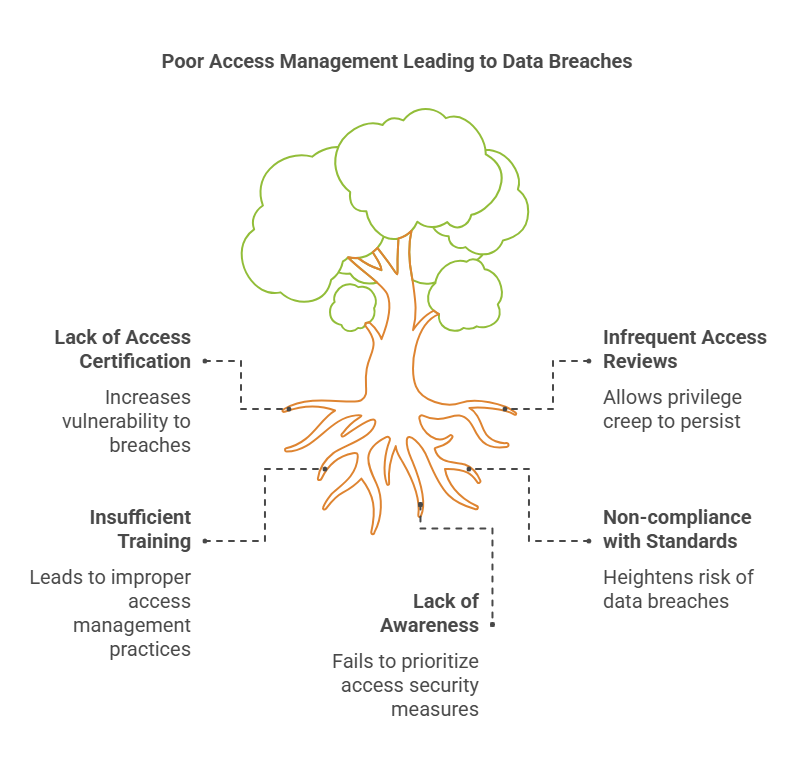
- A survey by Gartner indicated that over 65% of data breaches are linked to poor access management practices, including a lack of access certification.
- According to the Ponemon Institute, 74% of organizations report improved compliance readiness after implementing access certification processes.
- Organizations that regularly perform access certification see a 40% reduction in instances of privilege creep and associated risks.
FAQs
What is the primary goal of access certification?
The main goal is to ensure that users have appropriate access rights, minimizing risks associated with over-provisioned access.
How often should access certification be performed?
It depends on the organization’s risk appetite and compliance needs, but typically it is done quarterly or annually.
Who is responsible for conducting access reviews?
Usually, managers, system owners, or compliance officers are responsible for reviewing and certifying user access rights.
References & Further Reading
- SailPoint’s Guide to Access Certification
- Understanding the Role of Access Certification in Compliance
- Identity Management: A Comprehensive Guide by David G. White – An in-depth resource on IAM and access certification strategies.

0 Comments